Dubious Denials & Scripted Spin Spyware Company NSO Group Goes on 60 Minutes
by Miles Kenyon - Citizen Lab
April 1, 2019
Spyware developer NSO Group is usually quick to dismiss the evidence that its customers have abused its Pegasus mobile phone spyware.
“Don’t believe newspapers,” says NSO Group CEO Shalev Hulio
when asked about his role in selling NSO Group spyware to Saudi Arabia
(Image: CBS 60 Minutes).
This pattern of denial was repeated in a recent 60 Minutes investigation, which gives a rare look into NSO Group’s management.
60 Minutes correspondent Lesley Stahl got scripted spin and unsubstantiated denials when she confronted NSO Group’s CEO Shalev Hulio and co-president Tami Shachar with cases of abuse drawn from the evidence-based research of Citizen Lab, Amnesty International, and others.
Despite the misdirection, Stahl and 60 Minutes did extract some insights about the company:
- When questioned about the more than 29 publicly identified cases of abuse, NSO admits to only three
- NSO Group does not deny that it sold its Pegasus spyware to Saudi Arabia and will not explicitly deny that Jamal Khashoggi’s confidants were targeted with Pegasus
- NSO Group continues to spin and misdirect questions about abuses, particularly concerning the critical issue of allowing clients to define what constitutes “terrorism” and “crime.
As a reminder, Citizen Lab, Amnesty International, security companies, Google’s security team, and journalists have all contributed to building a picture of NSO Group’s powerful but abuse-prone technology. Pegasus, their signature spyware, is designed to infect and remotely monitor mobile phones. Once inside, operators have complete control of and access to everything in the phone, including encrypted messages, location data, and its microphone and camera.
Evidence Says at Least 30 Cases of Abuse; NSO Group Admits Three
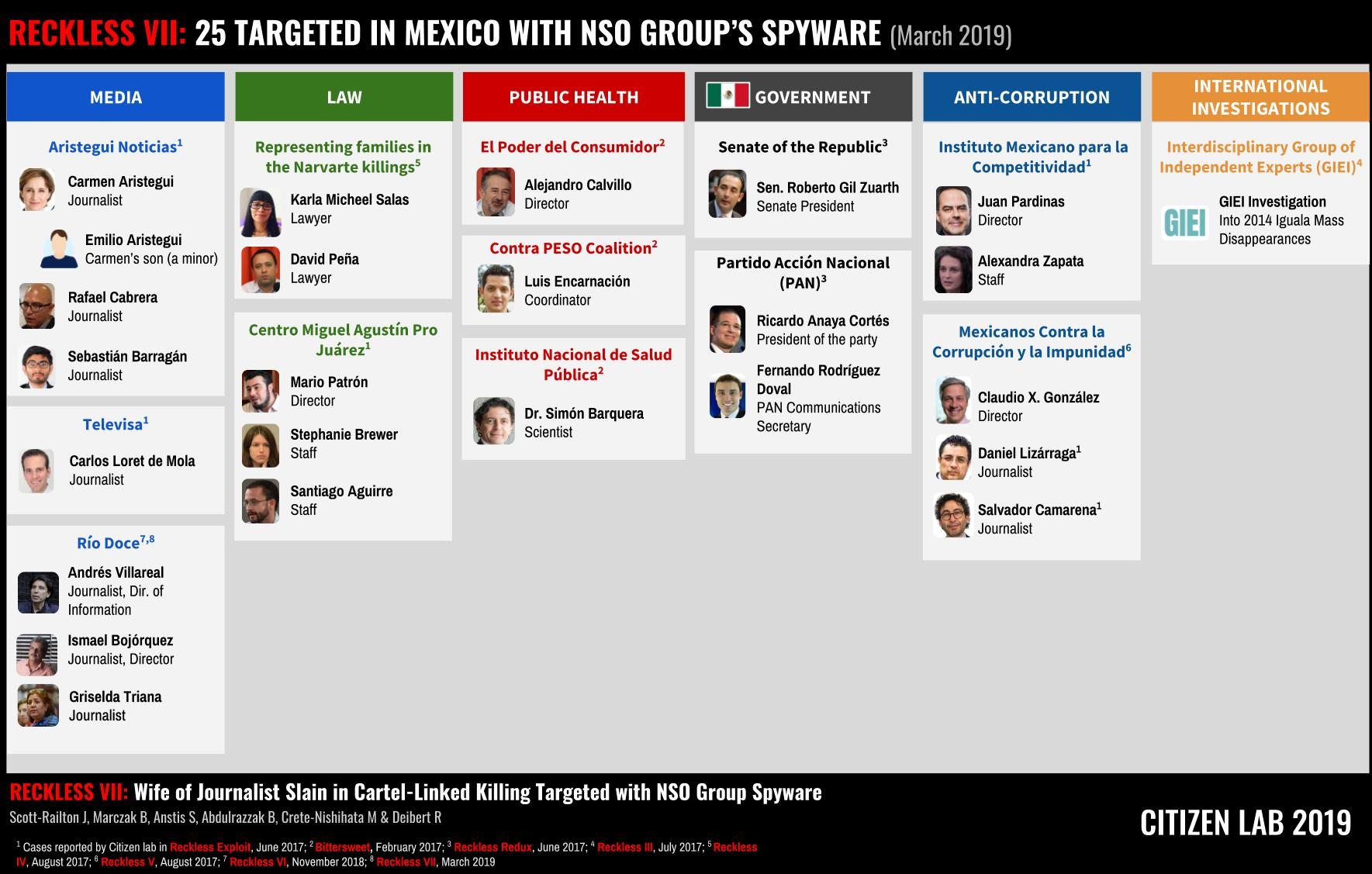
NSO’s CEO claims that there have been exactly three cases of abuse in the company’s history. But in Mexico alone, our research has identified more than 25 infection attempts against members of civil society. These targets include the phones of:
- A prominent Mexican investigative journalist who exposed a presidential corruption scandal and her minor child who was attending boarding school in the United States when he was targeted
- The widow of a Mexican journalist, targeted a week after her husband was assassinated in a cartel-linked operation
- Research scientists and health advocates promoting a tax on sugary beverages to help mitigate obesity issues
- International investigators into the mass disappearance of 43 Mexican students
Citizen Lab Director Ron Deibert (left) and Senior Research Fellow
Bill Marczak highlight the widespread use of NSO Group’s Pegasus
spyware by autocratic dictators and repressive regimes
(Image: CBS 60 Minutes).
Other research groups have identified even more cases of targeting with Pegasus, namely against an Amnesty International staff member and Yahya Assiri, and Ghanem al-Dosari, a Saudi comedian and government critic. None of these targets fit within the definition of a terrorist that Hulio says his customers adopt, namely “bad guys doing bad things in order to kill innocent people, in order to change the political agenda.”
Scripted Spin versus Facts on the Sale of Pegasus to Saudi Arabia
NSO Group CEO Hulio refused to provide an answer as to whether or not NSO Group sold Pegasus to Saudi Arabia, a country with a notoriously poor human rights record and for whom terrorist offences include insulting the reputation of the state.
When pressed by Stahl as to whether the sale happened, Hulio repeatedly deflected, stating that he did not want to speak about a “specific customer,” that NSO Group was “selling Pegasus in order to prevent crime and terror,” and that one should not believe news reports describing a trip Hulio took to Riyadh to sell Pegasus to the Saudis for $55 million. This seemingly scripted language has been oft-repeated by Hulio and the failure to actually deny a sale to Saudi Arabia is resounding.
Recently, journalist David Ignatius disclosed that, in fact, NSO Group has restricted its Saudi client’s use of Pegasus after an internal investigation determined that its spyware was not “directly” involved in the murder of Jamal Khashoggi. Such a finding is entirely consistent with Citizen Lab and others’ determinations that the Saudis were using Pegasus to spy on several of Khashoggi’s colleagues. In particular, Omar Abdulaziz (whose iPhone Citizen Lab determined was targeted with NSO Group spyware) and Jamal Khashoggi were exchanging what they thought were private WhatsApp messages about their plans for social media activism against Saudi autocracy.
Evidence of Abuses versus NSO Group’s Dubious Denials
Despite NSO Group’s pattern of questionable denials, research by Citizen Lab and peer organizations continues to surface new abuse cases and be replicated by additional research groups which arrive at the same conclusions. In an attempt to get a clear answer from NSO Group regarding their position on our research, we have sent numerous communications to the company and its investors (previously Francisco Partners, and, more recently, Novalpina Capital).
To date, NSO Group has failed to show that our research is flawed or erroneous in some way. Rather, the company continues to resort to outright denials without evidentiary support.
At least 25 cases of abuse have been documented in Mexico by
Citizen Lab and partner organizations R3D, SocialTic, and Article 19.
Ahmed Mansoor’s Targeting: Where It All Began
The 60 Minutes episode mentions our discovery that UAE dissident Ahmed Mansoor was a target of NSO spyware. In August 2016, Ahmed Mansoor sent us suspicious links in SMSs he received on his iPhone purporting to show evidence of torture in Emirati prisons. We infected a device in a laboratory setting and were able to acquire a copy of NSO Group’s Pegasus spyware.
With the assistance of the security company Lookout Inc, we reverse engineered the spyware and verified that it exploited three separate unpatched software flaws in the iPhone product.
We responsibly disclosed our findings to Apple Inc., who in turn pushed out security patches, securing about a billion users of Apple products worldwide. The “Million Dollar Dissident” report was the first ever published on NSO Group and is concrete evidence of the abuse of NSO Group spyware.
We would not have been able to get a copy of NSO Group’s Pegasus if Mansoor had not been targeted and Mansoor is neither a terrorist or a criminal. He is an award winning human rights defender. Sadly, Mansoor was recently sentenced to 10 years in prison and fined approximately $270,000 USD for criticisms of the regime he posted on social media.
From Spin to Spooks? Private Spies Targeting Citizen Lab, Litigants Against NSO Group
While NSO Group has made extensive attempts to paint themselves as concerned about accountability and abuses, we note two recent attempts to infiltrate the Citizen Lab and target our researchers by individuals with reported links to the Israeli-based private intelligence firm Black Cube.
We note that that the same operation targeted four other individuals all of whom happen to be involved in litigation relating to NSO Group.
The New York Times report on the case of a retired Israeli security
official linked to spy-for-hire firm Black Cube caught in a sting after
setting up a meeting under a false identity with a Citizen Lab researcher
(Image: New York Times).
While it is not publicly known who hired these spies, their activities were focused on (unsuccessful) efforts to trick our researchers into providing sensitive information about our investigations into NSO Group and making statements that could be used to discredit our work.



No comments:
Post a Comment